CEO Scam: How to Avoid the Bait…
August 11 2017CEO Scam: How to Avoid the Bait.
One day, Kemp; the CEO of Centrify cyber security company entered his office and decide to check the accounting department only for one of the employees to inform him “hey boss, were working on the wire transfer you requested”. Then he asked them “which transfer are you talking about? I did not request any transfer”. That is the point they realized that they can been scammed.
Upon a closer scrutiny, one of his accounting staff received an email purportedly from him and the company CFO Tim Steinkopf instructing them to transfer $357,000.
In the scamming email, the I and f had been flipped.
These are the kind of incidences that majority of company owners wake up to everyday. Fraudsters have devised new soft ways of stealing instead using the tiring and time consuming hacking strategies. They have realized that majority of employees do not question their bosses and only ask “how high” when they are told to “jump”.
CEO Scam among top 2016 Fraud related crimes
According to a report by the FBI regarding online frauds in 2016, CEO scam was among the top reported crimes.
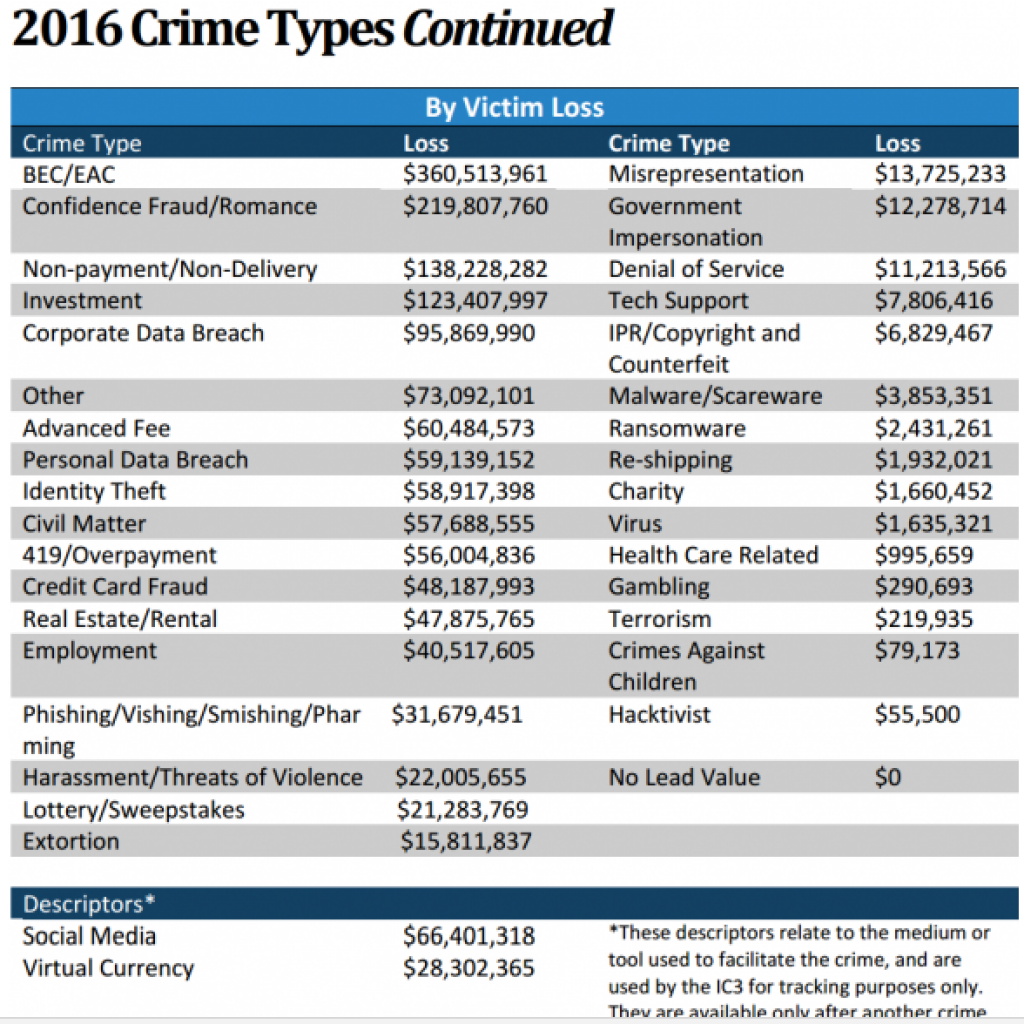
According to the report, a total of 17,146 extortion cases were reported where misrepresentation incidences led to a loss of $13 million.
CEO Scam
This is a scam where an email is sent from a source that seems to credible or from a known sender like a network administrator. These sender’s intentions is to dupe you into clicking into unsecure links to downloadable spyware or access login credentials through social engineering attacks.
Types of CEO Scam
Fraudsters uses several methods to commit to deceive their targets.
Phishing
This type of attack occurs when a phishing email is sent to many people at the same time in order to retrieve crucial information. The fraudsters impersonate legitimate sources and create look-a-like email format and design. Majority of the most impersonated companies include law enforcement companies, card providers and banks among others. The fraudsters work on the probability that among the many phishing emails sent, a few people will fall victim and respond.
Spear Phishing
This kind of phishing is more focused. The fraudsters conduct prior research on a victim behavior from social media, commonly used bank and card usage. In this case, the phishing email is personalized with the client’s name and this makes it look more legit.
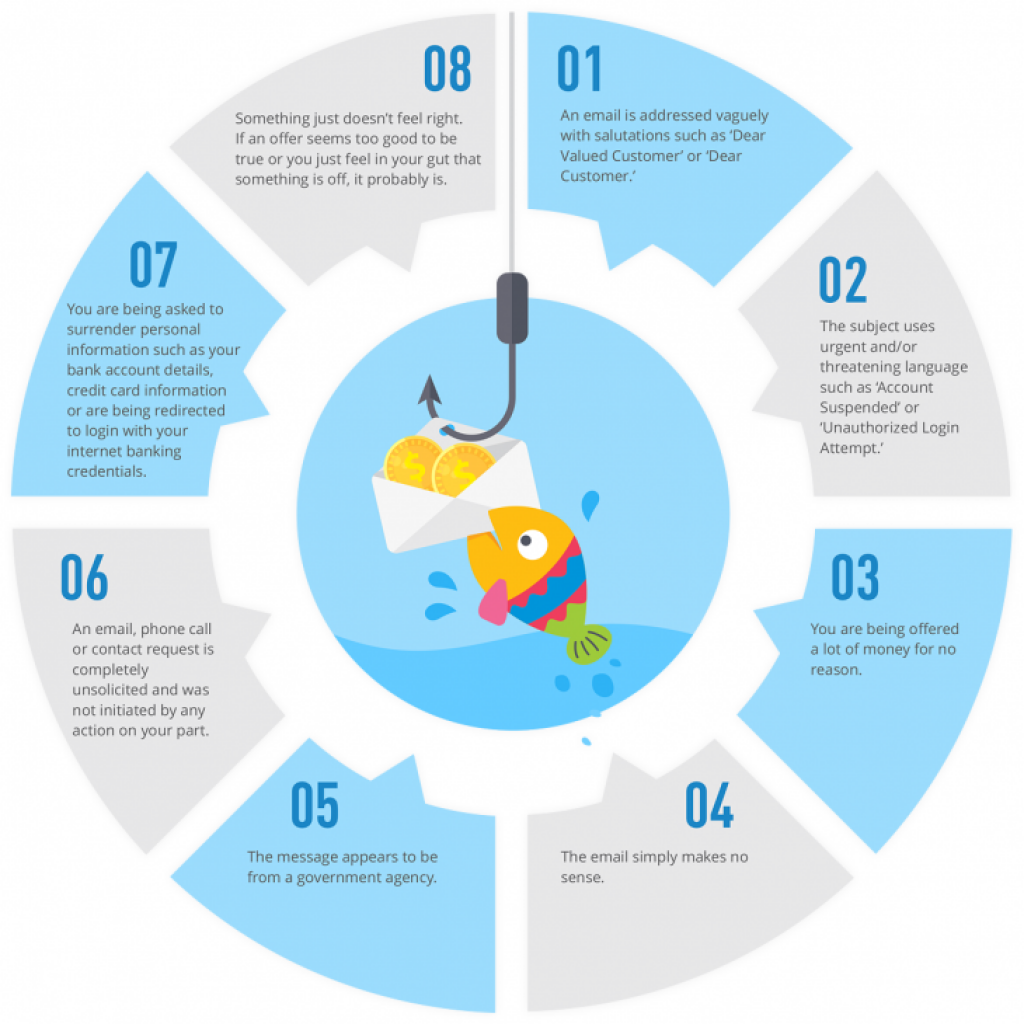
How to identify a spear phishing attack
- Forged links – confirm links on emails before clicking them. Mostly, suspicious emails are labeled by email filters as spams.
- Request for login credentials or personal information – formal and genuine emails do not request for personal information. Watch out for these kind of tricks.
- Sense of urgency – majority of hackers will trick you that a certain issue needs to be addressed urgently. This will make you give out personal information. Do not fall for this trick without confirming first.
How to prevent spear phishing attacks
- Avoid using similar or related passwords on different websites – using similar passwords increases the vulnerability once an attacker accesses one of your passwords.
- Avoid sharing personal information through social media or unsecure sources.
- Update your security software and patches regularly to avoid leaving loopholes for attackers to exploit.
- Security experts should train users on how to detect and report malicious emails.
- Use appropriate email security systems to secure your email servers.
Spear phishing attacks are common cases and currently are among the most very successful kind of attacks. Therefore, computer and network security departments should work over time to educate their users on how to avoid these kind of attacks.
CEO Scam: How to Avoid the Bait.
One day, Kemp; the CEO of Centrify cyber security company entered his office and decide to check the accounting department only for one of the employees to inform him “hey boss, were working on the wire transfer you requested”. Then he asked them “which transfer are you talking about? I did not request any transfer”. That is the point they realized that they can been scammed.
Upon a closer scrutiny, one of his accounting staff received an email purportedly from him and the company CFO Tim Steinkopf instructing them to transfer $357,000.
In the scamming email, the I and f had been flipped.
These are the kind of incidences that majority of company owners wake up to everyday. Fraudsters have devised new soft ways of stealing instead using the tiring and time consuming hacking strategies. They have realized that majority of employees do not question their bosses and only ask “how high” when they are told to “jump”.
CEO Scam among top 2016 Fraud related crimes
According to a report by the FBI regarding online frauds in 2016, CEO scam was among the top reported crimes.
According to the report, a total of 17,146 extortion cases were reported where misrepresentation incidences led to a loss of $13 million.
CEO Scam
This is a scam where an email is sent from a source that seems to credible or from a known sender like a network administrator. These sender’s intentions is to dupe you into clicking into unsecure links to downloadable spyware or access login credentials through social engineering attacks.
Types of CEO Scam
Fraudsters uses several methods to commit to deceive their targets.
Phishing
This type of attack occurs when a phishing email is sent to many people at the same time in order to retrieve crucial information. The fraudsters impersonate legitimate sources and create look-a-like email format and design. Majority of the most impersonated companies include law enforcement companies, card providers and banks among others. The fraudsters work on the probability that among the many phishing emails sent, a few people will fall victim and respond.
Spear Phishing
This kind of phishing is more focused. The fraudsters conduct prior research on a victim behavior from social media, commonly used bank and card usage. In this case, the phishing email is personalized with the client’s name and this makes it look more legit.
How to identify a spear phishing attack
- Forged links – confirm links on emails before clicking them. Mostly, suspicious emails are labeled by email filters as spams.
- Request for login credentials or personal information – formal and genuine emails do not request for personal information. Watch out for these kind of tricks.
- Sense of urgency – majority of hackers will trick you that a certain issue needs to be addressed urgently. This will make you give out personal information. Do not fall for this trick without confirming first.
How to prevent spear phishing attacks
- Avoid using similar or related passwords on different websites – using similar passwords increases the vulnerability once an attacker accesses one of your passwords.
- Avoid sharing personal information through social media or unsecure sources.
- Update your security software and patches regularly to avoid leaving loopholes for attackers to exploit.
- Security experts should train users on how to detect and report malicious emails.
- Use appropriate email security systems to secure your email servers.
Spear phishing attacks are common cases and currently are among the most successful kind of attacks. Computer and network security departments should work over time to educate their users on how to avoid these kind of attacks.




